With the selection of components in the previous step, you have defined the controls and threats which you find relevant for your risk assessment. The objective of this step is to document controls weaknesses you identify.
Testing your controls
For every control you will find guidance on how the control should be implemented. In the screenshot below, you can see the example of encrypting your AWS database (RDS).
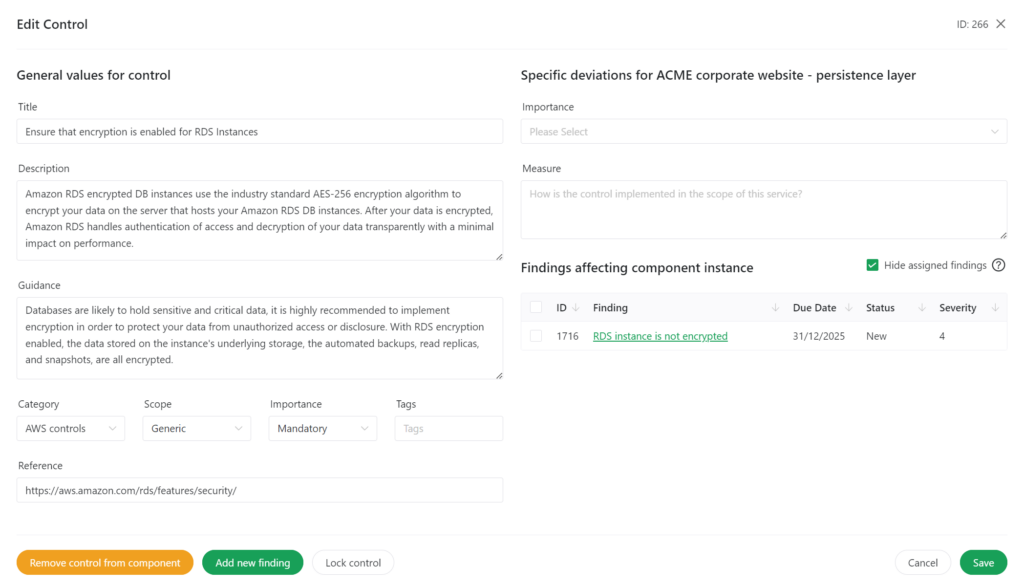
Documenting your results
Documenting your results is easy – in the screenshot above, you see an empty text area with the label ‘measure’. This would be the place to describe how the requirements on the left hand side of the screenshot have been implemented. If you realize that there is a gap, you document this gap as a security finding, for example like shown below:
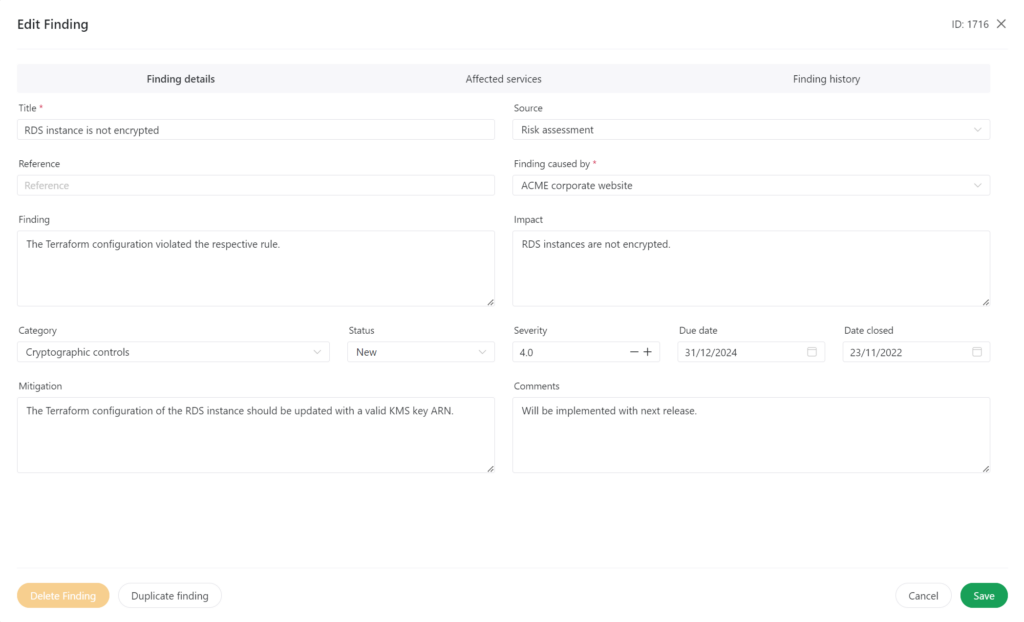
It is worth mentioning that findings can cause a risk for one or more systems, while being caused by a completely different system. This solves the problem of duplicating common findings for different systems, and it allows infrastructure findings to cause a risk for business systems, while still being assigned to the infrastructure team.

