Business Impact Analysis
A structured questionnaire helps you define the impact of breaches of confidentiality, integrity or availability.
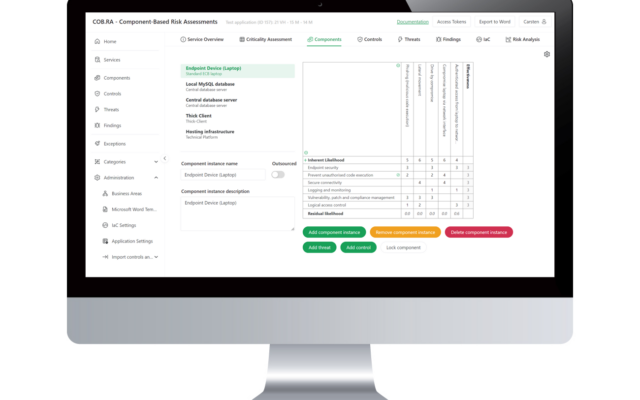
Component Libraries
Threats and controls are combined in reusable components – you choose the components you find relevant.
Track Control Weaknesses
Efficiently track security weaknesses, configure notifications and grant temporary exceptions for deviations.
Reporting Engine
Export any information to Microsoft Word, using a powerful template editing system.